Stay one Step Ahead of Hackers With Regular Security Audits.
Our Security Audit Platform was developed specifically for IT service providers to increase the security level of your company with targeted measures – and thus make your company an unattractive target for attackers.
Why Regular Audits are Crucial
Automated attacks, digitalization and the increasing complexity of IT infrastructures make it more and more difficult to keep track of the IT security situation.
The attack surface grows daily and the lack of visibility into your own IT security situation harbors risks. A single security gap can be enough for a hacker to penetrate your system unnoticed.
Regular checks are therefore necessary to quickly identify and fix vulnerabilities.
How it Works

Automated Security Audits of the Entire IT Infrastructure

Simple Assessment and Important Key Facts About the Security Situation

Customized Recommendations for Improving IT Security

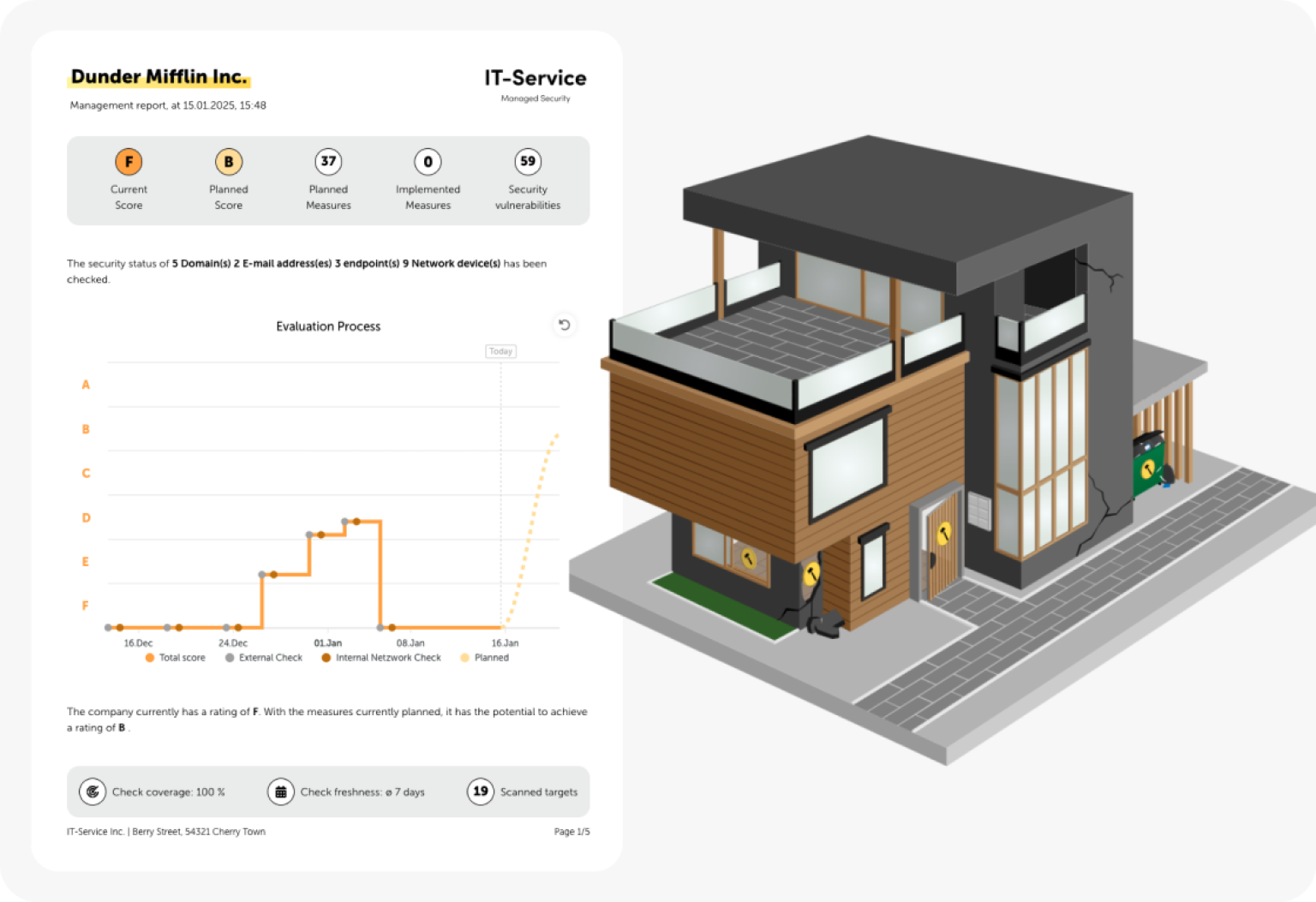
Compact Report and Presentation Using a House Analogy
Automated Security Audits of the Entire IT Infrastructure
With lywand, your IT service provider can regularly perform a comprehensive security audit – from the perspective of a potential attacker. Your external infrastructure, including (sub)domains, email addresses and IP addresses, is carefully analyzed for vulnerabilities and possible gateways. In addition, the service provider checks whether stolen company data appears on the darknet.
Your internal infrastructure, such as laptops and servers, is checked daily for common vulnerabilities and exposures (CVEs), best practice configurations and current patch levels using an agent. In addition, basic security mechanisms such as the Windows firewall, antivirus software and the use of Office macros are checked. With the Network Check, all network devices, such as printers and smartphones, are checked via a gateway.
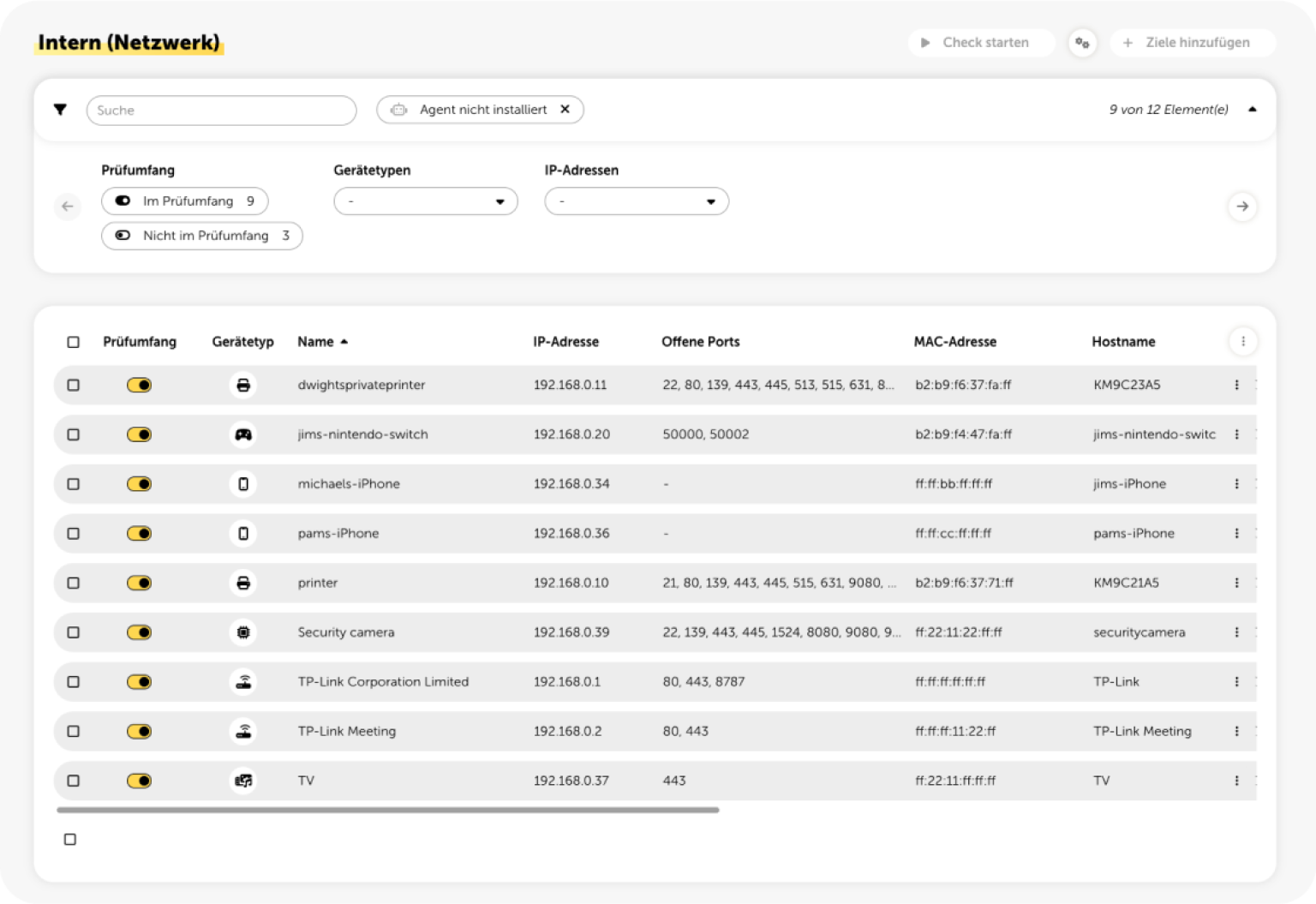
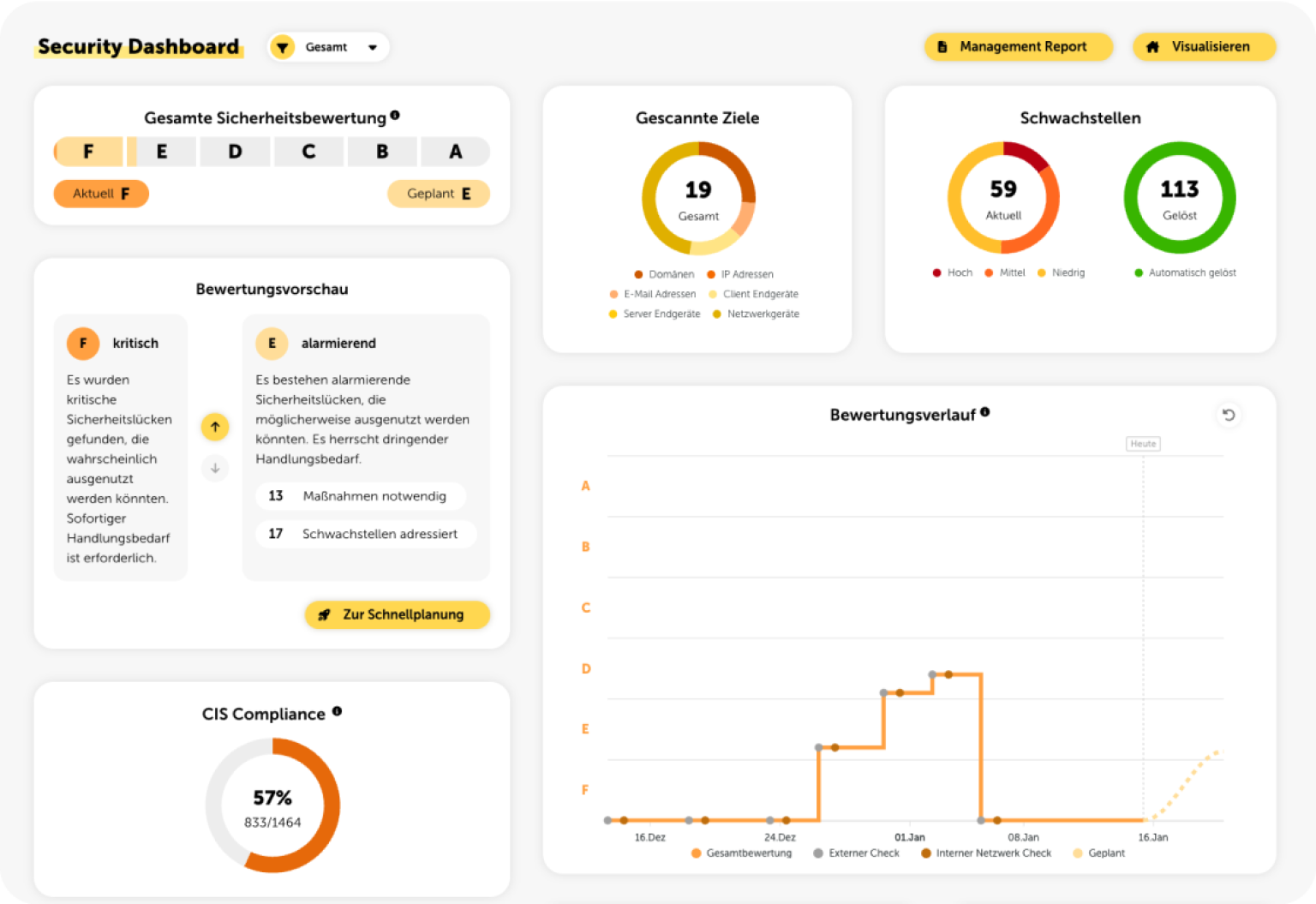
Simple Assessment and Important Key Facts About the Security Situation
After a security audit has been completed, the security status of your company is clearly displayed in the security dashboard. You will receive a general security assessment, which is supplemented by a detailed analysis of the vulnerabilities, including the number and distribution of risks.
The dashboard also shows the historical progress of the assessments, so that progress and trends can be clearly tracked. Particular attention is paid to the most vulnerable targets and products, as well as to an individual assessment of various security categories, such as passwords. This holistic presentation offers your IT service provider a well-founded insight into the actual state of your IT security.
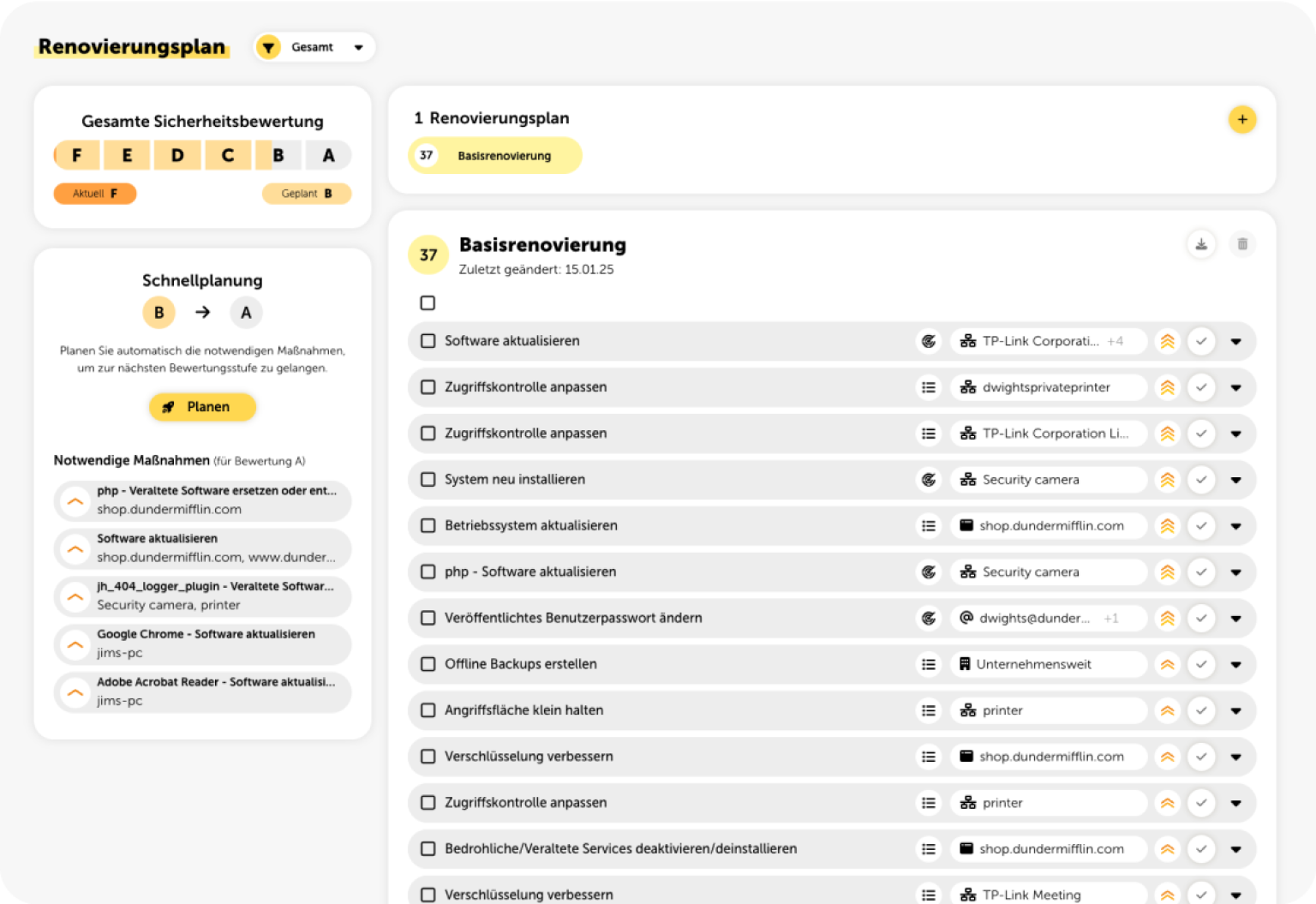
Customized Recommendations for Improving IT Security
Based on the results of the security audit, lywand provides specific recommendations for addressing the identified vulnerabilities. Your IT service provider will then discuss these suggestions with you, prioritize the next steps, and implement the measures in a targeted manner.
During the next security audit, lywand will check whether the implemented measures are actually effective and have closed the security gaps. This is how your company's security posture is improved in an effective and sustainable way.
Compact Report and Presentation Using a House Analogy
In the management report, we summarize the results of the security audit for you in a compact and easy-to-understand way. This provides you with a clear overview of the measures already implemented and the development of your security situation over time.
We have developed a house analogy to visualize the complex topic of IT security: security gaps are symbolized by open windows, doors or cracks in the facade. With the step-by-step implementation of measures, your IT service provider “renovates” your “digital house”, whereby the weak points gradually disappear.
What you can Count on
 Visibility of Your IT Security Situation
Visibility of Your IT Security Situation
Are there potential weak points that hackers could exploit to penetrate your system? Are the products used, such as virus protection, firewalls and patch management, configured correctly?
Regular security audits provide clarity and make your company's security situation visible.
 Concrete Security Measures to Minimize Your Attack Surface
Concrete Security Measures to Minimize Your Attack Surface
On the basis of the security audit, your IT service provider receives customized recommendations for action to eliminate the vulnerabilities found and to sustainably improve the security of your IT infrastructure.
These proactive measures can significantly reduce the attack surface and thus the risk of a successful hacker attack.
 Continuous Documentation of the Security Audits
Continuous Documentation of the Security Audits
With the monthly management reports, you regularly receive a reliable overview of your security situation.
This improves your starting position for certification processes or taking out cyber insurance. This can be particularly helpful in the event of a claim when dealing with regulatory issues.
Find the Right IT Service Provider
[ thefi.com ] GmbH & Co KG
thefi.com![[ thefi.com ] GmbH & Co KG](/en/img/asset/YXNzZXRzL2ltYWdlcy9wYXJ0bmVyL1stdGhlZmkuY29tLV0tZ21iaC0mLWNvLWtnLnBuZw/%5B-thefi.com-%5D-gmbh-&-co-kg.png?w=800&h=243&s=95f30b0d27f9fffa476c425c72cec64a)
4S IT-Solutions AG
4s-ag.de
admins4bit GmbH
admins4bit.com
Agentur Cyberschutz
cybercrime-komplettschutz.at
AKE IT-Services e.K.
ake-solutions.de
ALLinONE Netzwerke GmbH
allinone.de
AlpCloud GmbH
alpcloud.de
ALPHA‑Soft Computerservice GmbH
aszm.de
aptaro GmbH
aptaro.de
Arbor-Link GmbH
arbor-link.de
ARKTEC GmbH
ark-tec.de
AST GmbH
ast-gruppe.de
avanito GmbH
avanito.de
Backauf Computer GmbH
backauf.de
BADI Software und EDV-Systemberatung GmbH
badi.de
Becker IT und TK Service
becker-itk.de
BERGMANN engineering & consulting GmbH
bec.at
Berl EDV GesmbH
berl.at
BeSync AG
besync.ch/de
bis. itk GmbH
bis-itk.de
bitminder® GmbH & Co KG
bitminder.de
BITWINGS GmbH & Co. KG
bitwings.de
Blured Digital Technologies
blured.de
bridge4IT® e.K.
bridge4it.de
Brovko GmbH
http://www.brovko-consulting.de
BT Nord Systemhaus GmbH
btnord.de
Busse Computertechnik & Service GmbH
busse-computer.de
bytewerk GmbH
bytewerker.com
castus-iT GmbH
castus-it.at
CeeQoo e.U.
ceeqoo.com
cloudconnex GmbH & Co. KG
cloudconnex.de
Cobotec GmbH
cobotec.de
codekunst systems GmbH
codekunst-systems.com
Compatech GmbH
http://www.compa.tech
ConIT solutions Beratungs GmbH
conit-solutions.com
Connect Kommunikationssysteme GmbH
cnct.de
consult24 GmbH
consult24.at
coretress GmbH
coretress.de
cosmico GmbH
cosmico-it.de
CPX‑IT GmbH
cpx-it.de
CSG Systemhaus GmbH
csg-systemhaus.de
CS nine GmbH
cs9.at
CUBE33 GmbH
cube33.de
D-SYSTEME
d-systeme.at
Data at Work GmbH
daw.gmbh
Datec-Datentechnik GmbH
datec.jetzt
Dierck IT Systems GmbH
dierck-gruppe.de
DIGITAL ASSISTANCE e.U.
sichermit.at
dk-BITS GmbH
dk-bits.gmbh
DRAI Consult GmbH & Co. KG
draiconsult.de
EDVNeumann GmbH
edvneumann.de
E.S.H. Eichsfelder Systemhaus GmbH & Co. KG
e-systemhaus.de
EISENHUTH.NET GmbH
eisenhuth.net
emNETWORKS GmbH
emnetworks.net
enbiz engineering and business solutions GmbH
enbiz.de
esposito IT
esposito-it.de
eXemptec GmbH
exemptec.eu/#Home
exxo it-services AG
exxo.ch
Fix-IT Solutions GmbH & Co. KG
fix-its.de
Floitgraf Consulting GmbH
rene-floitgraf.de
FMComputer GmbH
fmcomputer.de
FP-Consulting e.U.
fpc.at
Franz Josef Strauß
melminsider.de/fjstrauss
Fusion IT GmbH & Co. KG
fusion-it.services
GCT mbH
gct.de
GEUDER Kommunikationstechnik GmbH
netzwerk-datenschutz-windsheim-ochsenfurt-rothenburg.de
gis-it GmbH
gis-it.de
Gleich IT Service GmbH
gleich-it.com
GOESYS AG
goesys.de
Gröpper IT-Systemtechnik GmbH
groepper-it.de
große Austing GmbH
austing-it.de
Grothe IT-Service GmbH
grothe-it.de
Hainke-Computer GmbH & Co KG
hainke.it
HELLTHO GmbH & Co. KG
helltho.de
hensec.eu
hensec.org
High5Manufaktur GmbH
h5m.de
HIT Computer GmbH & Co. KG
hit-computer.com
Hochwarth IT GmbH
hochwarth-it.de
HTH GmbH
hth-computer.de
ICO Innovative Computer GmbH
ico-systemhaus.de
ICOPA IT-Consulting Partner
icopa.de
ifaktor GmbH
ifaktor.de
ileven . it . cloudsolutions
ileven.at
INDUSYS GmbH
indusys.de
inet-tec
inet-tec.net/de
Intercept IT OHG
intercept-it.de
InterConnect GmbH & Co. KG
interconnect.de
ISG Informatik Service GmbH
isg-ro.de
IT Complete Systemhaus GmbH
it-complete.de
IT Consulting Kurrat
itc-kurrat.cloud
IT Eden
it-eden.de
IT Fabrik Systemhaus GmbH & Co.KG
it-fabrik.net
IT4U-Systemhaus GmbH
it4u-systemhaus.de
itex it-service GmbH
itex.at
itmc GmbH
itmc.de
IT Point Network Solution GmbH
itpoint.de
ITs-plus GmbH & Co. KG
its-plus.de
JOBA ITK-Systeme GmbH
joba.info
jo-soft GmbH
jo-soft.de
JT-Computer Soft- und Hardware HandelsgesmbH
jtnext.at
Karpo GmbH
karpo.gmbh
keepbit IT-SOLUTIONS GmbH
keepbit.de
KEP-Consult GmbH
kep-consult.com
kernzeit AG
kernzeit.com
KlarBIT GmbH
klarbit.de
klip-asca GmbH
klip-asca.de
Kurnol + Wohlfahrt Elektronik GmbH & Co. KG
kuw-net.de
Kutzschbach Electronic GmbH & Co. KG
kutzschbach.de
L+S IT Services GbR
lunds-it.de
Lendeckel IT GmbH & Co. KG
lendeckel-it.de
LHL Computer-Service GmbH
lhl-service.de
LOGOsoft Computer GmbH
logosoft.org
M IT-Systemhaus GmbH
m-itsysteme.de
Make IT fix GmbH
makeitfix.com
Matt EDV GmbH
matt-edv.com
MBCOM IT-Systemhaus GmbH
mbcom.de
MC-Netzwerke GmbH & Co. KG
mc-netzwerke.com
mea IT Services e.U.
mea-it.services
MECO Systemhaus GmbH
meco.de
MicroVation GmbH
microvation.de
mits group GmbH
mits-group.de
mocotel services
mocotel.de
Modern Workplace GmbH
modern-workplace.de
MOTIONDATA VECTOR Software GmbH
motiondata-vector.com
MR Elektronik GmbH & Co. KG
mr-elektronik.net
MT Service GmbH & Co KG
mt-edvservice.at/computer-woergl-kufstein.html
MXP GmbH
mxp.de
myDC Cloud Services GmbH
mydatacenter.at
NCC Systems GmbH
ncc-systems.de
NCE Computer GmbH
nce.de
netable IT & Digitalisierungsservice V. Frank
netable.de
Netmicro e.K.
netmicro.eu
NetWerk Internet Intranet Services GmbH
netwerk.de
NetWorxx EDV Services GmbH
http://www.networxx.at
NewWay.IT GmbH
new-way-it.de
OBF IT-Solutions GmbH & Co. KG
obf-it.de
Opexa Advisory
opexaadvisory.de
optimio AG
optimio.com
PC-SPEZIALIST Hannover
pcspezialist.de
PCDsystems GmbH & Co. KG
pcd-systems.de
PRinguin GbR
pringuin.de
project two gmbh
projecttwo.de
Protego 24 Sicherheitsservice GmbH
freihoff-gruppe.de
Purple‑Tec IT Services GmbH
purple-tec.at
Q-Data Service GmbH
qds.de
Qberos GmbH
qberos.org/index.html
Quadus GmbH
quadus.de
RCYBER.de
rcyber.de
RioMar GmbH
riomar-it.de
rockIT AG
rockit.ch
emvion IT Solutions GmbH & Co. KG
emvion.de
Sartissohn GmbH
sartissohn.de
Schönsee Loosen Datentechnik GmbH & Co. KG
sld.de
Select-IT Beratung und IT-Dienstleistung GmbH
select-it.at
sevian7 IT development GmbH
sevian7.com
Siedl Networks GmbH
siedl.net
sigmavista it consulting gmbh
sigmavista.com
Simon Fieber IT-Services
simonfieber.it
SIS Systemhaus GmbH
sis-systems.de
smart.net.works GmbH
smart-net.works
SPIDER Netzwerk Consulting GmbH
spidernet.at
SPS Informationstechnologie GmbH
sps-it.de
Stan-IT
stan-it.de/startseite.html
Stauffer - Medien & IT GmbH
mit-stauffer.de
Systemhaus Przykopanski
przykopanski.de
Systemschub – Eine Marke der Klaes GmbH & Co. KG
systemschub.de/home
Technical Support Telekommunikation & IT
techsup.de
Techniklotsen gGmbH
techniklotsen.de
TECHWAVE GmbH
techwave.at
Tecvise GmbH
tecvise.de
Tiersch & Co. GmbH
tico.de
toolbox Systemberatung GmbH
toolbox.at
Truttenbach.IT GmbH
truttenbach.it
up to date gmbh
uptodate.at
WAPP IT! Solutions AB GmbH
wappit.de
web&IT Solutions
web-and-it.com/welcome
WeQ technologies GmbH
weq-tech.at
Weser-Ems Dataconsulting GmbH
wescon.de
wistuba it GmbH
wistuba-it.com
WKN Datentechnik GmbH
wkn-datentechnik.de
WorldWideWAN GmbH
wwwan.de
xenonet by Hartmann
xenonet.de
Google Maps cannot be displayed.
As Google Maps is a third-party software, cookies must be accepted for this.
Frequently Asked Questions
Small and medium-sized companies are increasingly the target of cyber attacks. The attack surface is growing due to digitalization, home offices, automated attacks and the increasing complexity of IT infrastructure. Ignoring these risks can have serious consequences.
Strong cybersecurity is more important today than ever. We offer you automated and continuous security checks that identify security vulnerabilities and suggest appropriate measures for closing them.
To provide you with comprehensive cyber security, we work with IT service providers who will advise and support you individually. This support minimizes your effort so that you can concentrate on your core business.
We work exclusively with IT service providers, system houses and MSSPs. These experts will be happy to provide you with a tailor-made offer.
The costs depend on the size of your IT infrastructure and your individual requirements. Your IT service provider will be happy to provide you with a customized offer that is tailored to your needs.
If you are interested in our product but your current IT service provider does not yet offer it, we can help!
Simply provide us with the contact details of your IT service provider and we will contact them directly to discuss the possibilities of working together.
This is What lywand Stands for
Contact Us
Please feel free to use our contact form to send us a message.
Lywand Software GmbH
Headquarter
Josefstraße 46a/6
3100 St. Pölten, Austria
