Curious?
In a short video, you can get to know the most important features at once.
Or would you like to learn more? We’d be glad to give you a closer look at the platform in a personal meeting.
We use cookies to give you the best experience on our website. You can choose which cookies you want to allow below. You can find more details in our privacy policy.
Purpose | So that the user's cookie preferences can be taken into account, these are stored in the cookies. |
Data | Accepted or rejected cookie categories |
Originator | Lywand Software GmbH |
Privacy Policy |
Purpose | This web analytics tool allows us to compile user statistics about your website activity and to best tailor our website to your interests. |
Data | anonymized IP address, pseudonymized user identification, date and time of the request, amount of data transferred incl. message as to whether the request was successful, browser used, operating system used, website from which access was made. |
Originator | Google Ireland Limited |
Privacy Policy |
Purpose | Representation of the company's location using Google's map service. |
Data | Date and time of visit, location information, IP address, URL, usage data, search terms, geographic location. |
Originator | Google Ireland Limited |
Privacy Policy |
Purpose | Convenient appointment scheduling via Calendly directly on the website. |
Data | Appointment information, calendar information, information from third-party software providers, payment information, chatbot data, marketing information, log & device data, cookie data, usage data |
Originator | Calendly LLC |
Privacy Policy |
Purpose | This data processing is performed by YouTube to ensure the functionality of the player. |
Data | Device information, IP address, referrer URL, viewed videos |
Originator | Google Ireland Limited |
Privacy Policy |
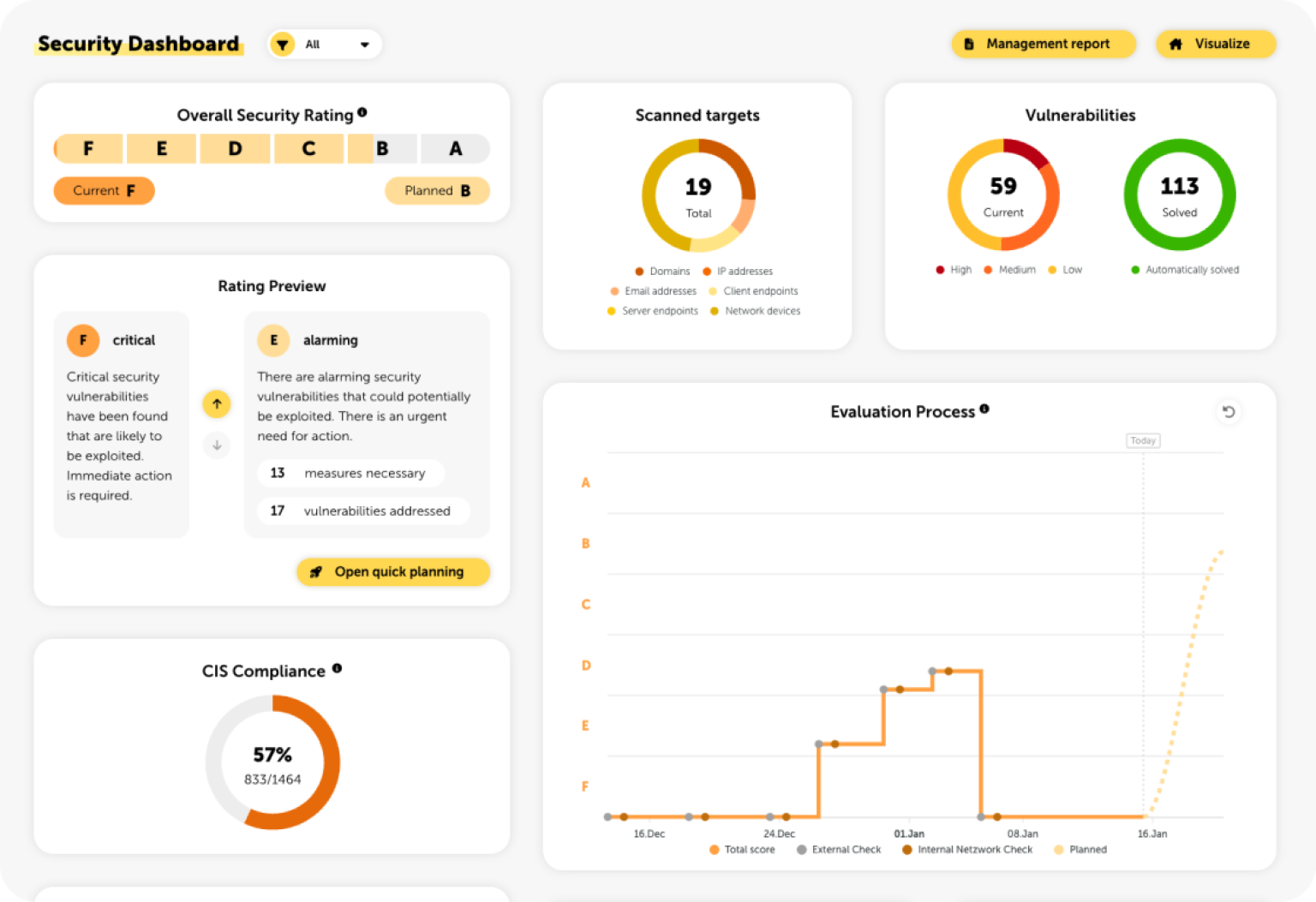
Lywand takes care of ongoing security assessments for you – automatically and reliably. This lets you stay on top of risks, measurably improve your customers’ security, and increase the quality of your services.
Shows at a glance how vulnerable the publicly accessible infrastructure is. Domains, IPs, and email addresses are analyzed to detect vulnerabilities and compromised accounts early.
Examines all Windows clients and servers in detail: vulnerabilities, configurations, patch levels. Plus automatic asset discovery for complete network transparency.
Analyzes all devices in the internal network via a gateway. You quickly see where vulnerabilities and configuration issues are hidden – or where essential system hardening is missing.
The External Check provides a fast and straightforward entry into security analysis. It reveals how vulnerable a company’s externally reachable infrastructure is – exactly where potential attackers would probe first. This includes checking domains and subdomains, public IP addresses, and email addresses.
Lywand performs a comprehensive security assessment from an attacker’s perspective and identifies:
Common Vulnerabilities and Exposures
Configuration and encryption standards
Web security according to OWASP Top 10
Compromised email addresses from password leaks
In addition to the external security posture, it’s important to keep internal IT infrastructure in view. For this, lywand uses its own agent – software installed on compatible Windows clients and servers.
The agent thoroughly analyzes each system and checks:
Common Vulnerabilities and Exposures
Misconfigurations
Current patch levels
Implementation of basic security mechanisms
(e.g., firewall enabled, antivirus present, handling of Office macros)
Alongside the security analysis, the agent automatically performs asset discovery.
It detects and inventories all devices reachable in the network – from laptops and servers to smartphones, printers, and other network devices.
This creates full transparency across the existing IT infrastructure, making forgotten or unknown devices visible.
Last but not least, the Network Check allows you to assess the entire internal network for vulnerabilities – from printers and smartphones to Linux and macOS systems. The security assessment is carried out via a dedicated gateway deployed as a virtual machine inside the network.
This check uses several methods to assess security:
Common Vulnerabilities and Exposures
Configuration and encryption
System hardening

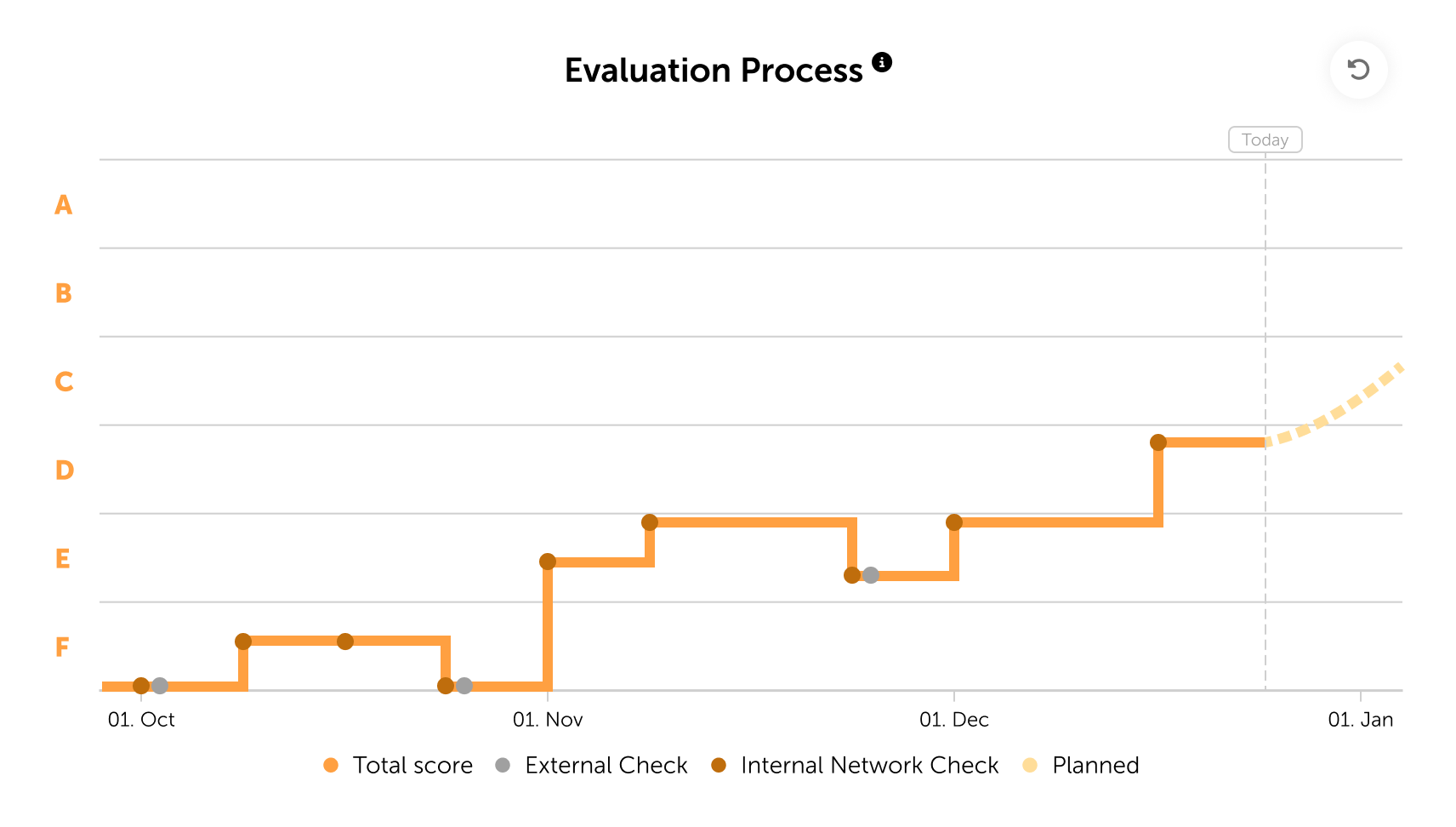
If the rating worsens after a security audit, you will automatically be notified by email.
This allows you to respond immediately before small issues turn into major risks.

IT security is dynamic. With lywand, you can schedule automated, recurring assessments.
Define frequency, weekday, and time – lywand handles the rest.

You can start a security assessment at any time – for the entire scope or specific systems.
This is especially useful for checking whether vulnerabilities have actually been fixed after implementing measures.
In a short video, you can get to know the most important features at once.
Or would you like to learn more? We’d be glad to give you a closer look at the platform in a personal meeting.