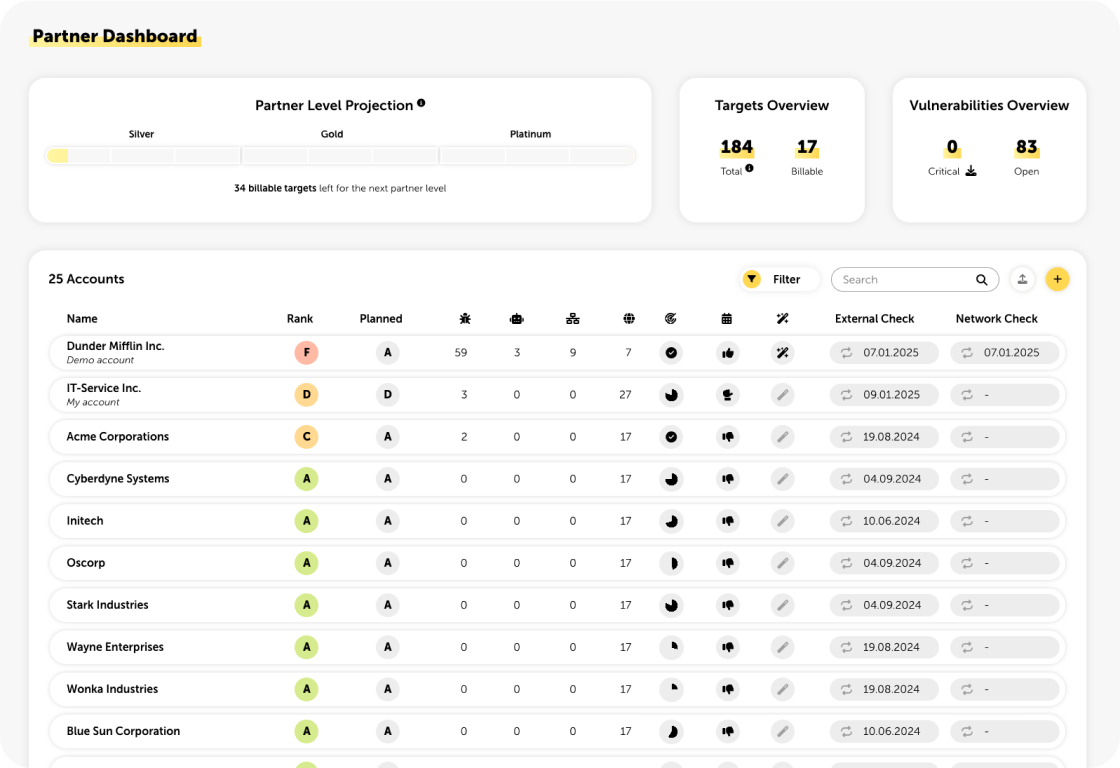
A Platform Tailored to Your Needs.
Developed by IT security experts for MSSPs, IT service providers and system houses.
Automated Security Checks
Perform regular security checks for your customers at freely selectable intervals – enabling continuous analysis of the IT infrastructure for potential vulnerabilities.
Three types of automated checks are available:
External Check for domains, IPs, and email addresses
Agent Check for Windows servers and clients
Network Check for the entire internal infrastructure such as printers, smartphones, Linux, and Mac devices
Clear Rating & Key Insights
After completing a security audit, the IT infrastructure receives a rating, and the current security status is presented in a clear and structured way.
The progression of these ratings makes developments and improvements easy to track. Systems, products, and key categories that are particularly at risk are highlighted – providing a holistic understanding at a glance.
Practical filtering options also allow for a separate evaluation of your Managed Services – making the value of your services more visible and creating easier opportunities for upselling.
Automatic Remediation of Vulnerabilities
With Auto Healing, up to 80% of detected vulnerabilities can be automatically fixed after an Agent Check – entirely without manual effort.
You can define individually for which devices and under which conditions Auto Healing should be active, for example only on specific device types or only for minor updates. The execution time can also be flexibly scheduled.
Supported applications include Microsoft Windows Suite, Java, Firefox, and Foxit PDF Reader.
Effective Measures for Remaining Risks
Based on the audit results, recommendations for improving security are provided, including clear descriptions and step-by-step instructions.
These measures are prioritized across all customers, making it immediately clear which actions have the greatest impact on the overall security posture.
In addition to centralized planning and progress tracking, lywand automatically verifies the effectiveness of implemented measures after completion.
Furthermore, the Renovation Plan is also available at the customer level, where recommendations are individually tailored.
Concise Report & House Analogy
To help you present results to your customers in a clear and convincing way, lywand offers two formats:
Management Report – summarizes all relevant information in a concise and understandable manner for decision-makers.
House Analogy – designed for customers who are less technically experienced. It visualizes IT security in simple terms – for example, an open front door may represent an insecure password, while a crumbling façade symbolizes misconfigurations. This way, customers can instantly see where action is needed.
Numerous Features for Greater Efficiency in Everyday MSP Operations
Seamless Integration into Ticketing Systems
With integrations to Autotask PSA, TANSS and c-entron, you can keep track of all measures. Synchronization ensures that tickets are created and seamlessly monitored.
Versatile Opportunities with Open API
Our open API allows you to seamlessly integrate lywand into your processes – whether for ticketing systems, communication platforms, or other applications.
Custom Branding with Whitelabeling
Design the platform in your company’s own look and feel. With Whitelabeling, you can customize the color scheme, logo, system emails, and login URL to match your brand.
Read-Only Access for Customers
With read-only access, you can provide your customers with secure insight into their IT security status – without allowing any changes to be made.

Now It’s Time to Settle the Bill
To support you optimally in your service offering, we use a consumption-based billing model that charges the actual usage based on the targets you have checked.

Pay-as-You-Go Billing
Billing is based on the security checks performed and the respective scope of each check.

Independent of Customers
There are no customer-related licenses. All completed checks are aggregated across all customers and billed as consumption.

Three Partner Levels
Your partner level increases with your usage and automatically improves your purchasing conditions. The higher the level, the more attractive the pricing.
Flexible and Without Commitment
There are no minimum quantities and no contract terms. Billing is done monthly, and only for what was actually used.

Billing Through Distributor
At the end of the month, you receive the invoice directly from your distributor, broken down by customer.